👋 Hey friends,
This week’s update is short but solid. Here’s what I’ve got for you:
Another peak into Chapter 3 of The Backend Lowdown
Launched my personal site
Video deep dive: The Egress Rule That Broke Everything
Tool highlight: Astro.js
Let’s get into it! 👇
The Backend Lowdown: Chapter 3 Preview
Every newsletter will include a snippet from my book in progress, The Backend Lowdown, available for $1 right now on Gumroad!
How to Prevent N+1s
What's better than getting rid of N+1 queries? Not having them in the first place, of course. There are a few ways to go about this, depending on the API you're working on. Here are the most reliable prevention strategies across different types of backends.
Eager Loading Best Practices
Eager loading means telling your ORM to fetch associated data up front, in the same database query (or a small set of known queries), instead of waiting until you access it later. As mentioned, most ORMs use lazy loading by default. That means if you call author.books inside a loop, the books won't be fetched until that line runs, causing a new query for every author. Eager loading flips that around. You load everything you need in one go, before entering the loop.
# Without eager loading - triggers N+1
authors = Author.all
authors.each { |a| puts a.books.count }
# With eager loading - avoids N+1
authors = Author.includes(:books).all
authors.each { |a| puts a.books.count }The performance difference is huge: instead of making 101 queries to render 100 authors and their book count, you'll make just 1 for authors + 1 for all books.
Note
There are different ways to eager load associated records and each way has its own nuance. We won't dive into the specifics here as it will vary based on the ORM, but as an example, Rails also gives you preload and eager_load. They all preload data differently depending on context.
My Personal Site is Live!
It’s small, but I finally launched stevencodes.dev. A place to point people when they ask “where can I find your stuff?”
Let me know what you think - or if there’s anything you’d like to see added.
Fun fact: TikTok throws a big scary warning when you use a personal domain in your profile link 😅 So I’m keeping my Linktree up for now.
Video Deep Dive: The Egress Rule That Broke Everything
This one hit a nerve: I shared a triage quiz about a production incident caused by removing a single egress rule.
Port 443 got blocked, and suddenly everything depending on HTTPS started to fail.
Let’s break down what happened in this video step by step, including the rationale behind the debugging methodologies to determine the root cause.
The Core Scenario
You’re paged at 3:07 AM: payment-service: third-party API calls failing – ECONNREFUSED. On the bastion host you run:

curling Stripe’s API
But from your laptop, it works. A quick diff of last hour’s Terraform reveals the outbound security group rule for port 443 was removed, blocking HTTPS to every third-party API.
Minor Correction: Timeout Instead
As Joe here correctly pointed out, there was a slight issue with this scenario: you likely would get a connection timeout instead of ECONNREFUSED.

What Is a Bastion Host?
A bastion host (or “jump box”) is a hardened server that sits in a public subnet and provides the only entry point into your private network. By funneling all SSH connections through one well-secured machine, you minimize your attack surface and keep private instances shielded from direct internet exposure.
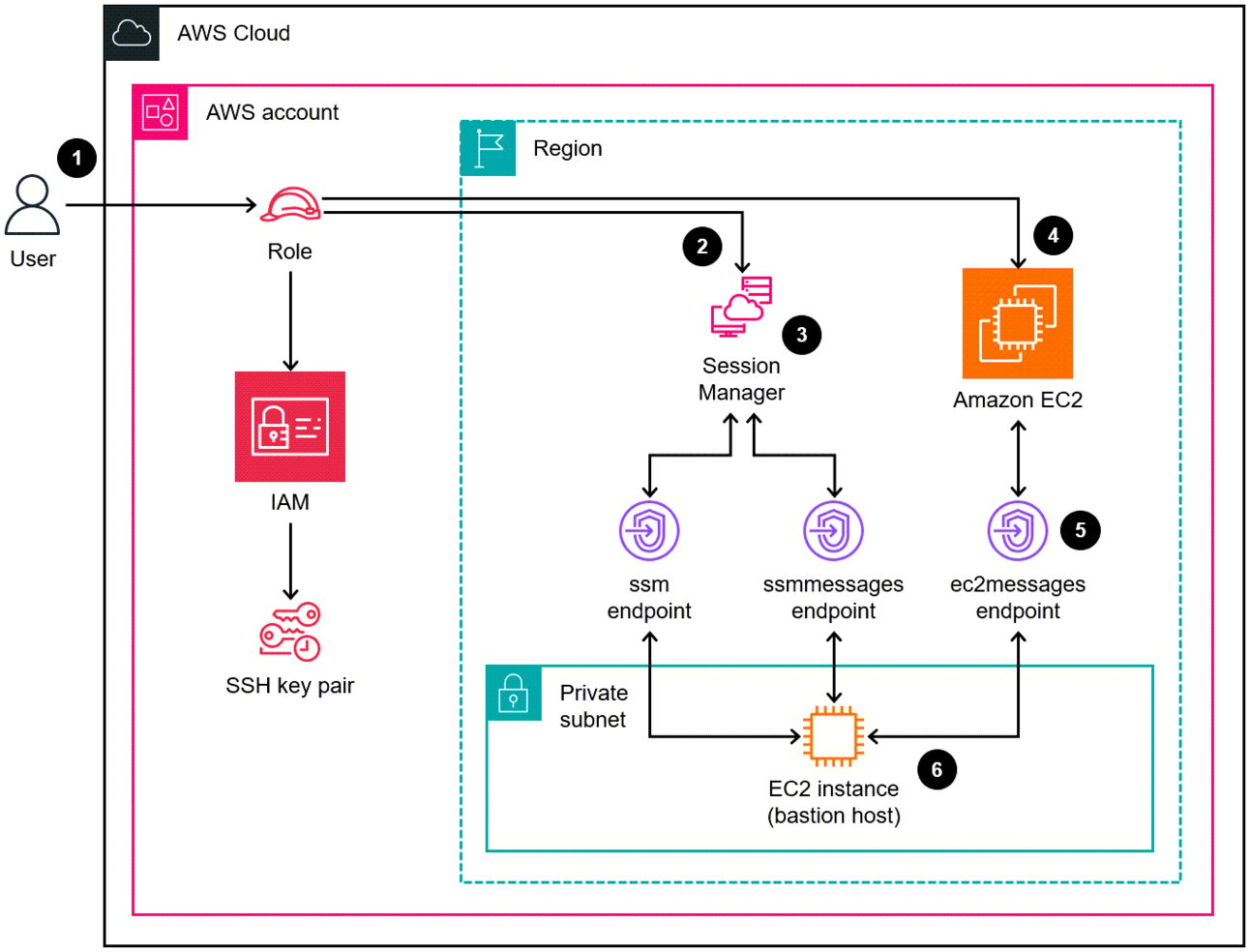
AWS example of a bastion host (EC2 instance at the bottom)
Why Curl from the Bastion, Then Your Laptop?
On the bastion host: You’re inside the VPC’s (Virtual Private Cloud) private subnet, subject to its security groups. When port 443 egress is blocked,
curlthere fails with “Connection refused.”On your laptop: You’re outside the VPC altogether, so you bypass those security-group restrictions and the same request succeeds.
This dual check quickly confirms that the issue isn’t Stripe or the internet at large, but your VPC’s firewall rules.
After doing the above, you then scanned the last hour’s Terraform diff to discover that an egress rule for port 443 was removed and was the root cause of the issue.
What Is Terraform?
Terraform is an Infrastructure as Code (IaC) tool that lets you define, change, and version cloud infrastructure in declarative HCL files. Instead of clicking around in a console, you store your network, compute, and security configurations as code, giving you auditability, repeatable builds, and easy rollbacks.
Why Option A (Rolling Back) Fails
Since the root cause was a missing outbound rule in the security group, not a buggy code release, rolling back the image wouldn’t restore HTTPS access. You must fix the infra (security group) directly.
Why Option B (Restarting NAT Gateway) Fails
First of all, what is a NAT Gateway? A NAT gateway is a managed AWS service that sits in a public subnet and performs Network Address Translation for instances in private subnets. It lets those instances initiate outbound connections to the Internet (or other VPCs) without allowing inbound traffic from the Internet back to them.
As for why this would not resolve the issue, the bottom line is that security groups act as virtual firewalls on each network interface (ENI) attached to your instances. Even if the NAT gateway were perfectly healthy, your bastion host’s ENI still has an outbound rule denying TCP/443. The packet never reaches the NAT gateway to be translated, AWS refuses it at the instance layer.
Why Option D (Switch to HTTP/2) Fails
HTTP/2 is simply a more efficient wire-format for HTTP featuring header compression, multiplexed streams, and server push. It cannot bypass a firewall rule that outright blocks port 443. Even if your client and server speak HTTP/2 perfectly, the TCP handshake on a firewalled port will still be refused.
The One True Fix: Option B
Re-apply the egress rule for port 443. Instant HTTPS connectivity is restored, and all your third-party integrations spring back to life.
Lessons Learned
Smoke-test from inside AND outside your VPC to pinpoint DGW vs. internet issues.
Guardrail your security groups with plan-approval gates or AWS Config rules to prevent drift.
Automate drift detection (e.g., Terraform Cloud’s Sentinels or AWS Config Rules) so you’re alerted before prod breaks.
Watch the video here:
@stevencodes.swe Third party API calls failing with ECONNREFUSED? See if you can figure out the right action to fix this backend triage issue! Leave your g... See more
Tool Highlight: Astro.js
I built my new site with Astro.js - a Node-powered static site generator that ships zero JavaScript to the browser by default. That means static-site speed and SEO with optional interactivity only where you need it.
If you want a modern-feeling site with the performance of pure HTML/CSS, Astro is worth a look.
That’s a wrap for this week. If something here made your day smoother, feel free to reply and tell me about it. And if you think a friend or teammate would enjoy this too, I’d be grateful if you shared it with them.
Until next time,
— Steven
P.S. Thinking About Starting a Discord…
A few folks have asked if I’d ever make a Discord for backend/dev talk, questions, content ideas, etc.
I’m thinking about it.
Not promising anything just yet, but if that’s something you’d be into, reply and let me know. It helps me gauge interest!
